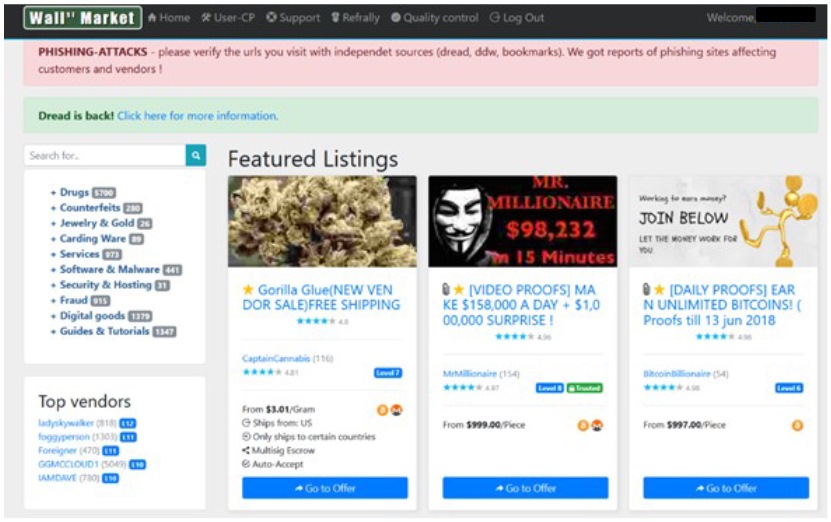
The major darknet marketplace known as the Wall Street Market have been seized and its alleged operators arrested in a joint operation between European and U.S. authorities. Millions in cash, cryptocurrency, and other assets were collected, and the markets shut down. How investigators tied these anonymity-obsessed individuals to the illegal activities is instructive.
The three men accused of running Wall Street Market (WSM), one of the larger hidden service markets operating via the Tor network, are all German citizens: Tibo Lousee, Jonathan Kalla, and Klaus-Martin Frost; several vendors from the market have also been charged, including one who sold meth on it by the kilogram.
The investigation has been ongoing since 2017, but was pushed to a crisis by the apparent attempt in April by WSM’s operators to execute an exit scam. By suddenly removing all the cryptocurrency held in escrow and otherwise stored under their authority, the alleged owners stood to gain some $11 million if they were able to convert the coins.
Until recently Wall Street Market was a bustling bazaar for illegal goods, including dangerous drugs like fentanyl and physical items like fake documents. It had over a million user accounts, some 5,400 vendors, and tens of thousands of items available for purchase. It has grown as other darknet marketplaces have been cornered and shut down, driving users and sellers to a dwindling pool of smaller platforms.
 Whether the owners sought simply to parley this growth to a quick cash grab or whether they sensed the law about to knock down their door, the exit scam was undertaken on April 16.
Whether the owners sought simply to parley this growth to a quick cash grab or whether they sensed the law about to knock down their door, the exit scam was undertaken on April 16.
This action prompted investigators in the U.S., Germany, and Europol to take action, as this exit scam marked not only an opportunity for investigators to gather and observe fresh evidence of the trio’s alleged crimes, but waiting much longer might let them go to ground and launder their virtual goods.
The DOJ complaint details the means by which the three administrators of the site were linked to it, despite their attempts to anonymize their access. It isn’t unprecedented stuff, but it’s always interesting to read through the step-by-step forensics that lead to charges, since it can be very difficult to tie real-world actors to virtual entities.
For Frost, it was an unstable VPN connection that did for him, plus some sleuthing by the German federal police, the Bundeskriminalamt or BKA:
The WSM administrators accessed the WSM infrastructure primarily through the use of two VPN service providers. On occasion, VPN Provider #1 connection would cease, but because that specific administrator continued to access the WSM infrastructure, that administrator’s access exposed the true IP address of the administrator
The individual utilizing the above-referenced IP address to connect to the WSM infrastructure used a device called a UMTS-stick (aka surfstick) [i.e. a dongle for mobile internet access]. This UMTS-stick was registered to a suspected fictitious name.
The BKA executed multiple surveillance measures to electronically locate the specific UMTS-stick. BKA’s surveillance team identified that, between February 5 and 7, 2019, the specific UMTS-stick was used at a residence of Lousee in Kleve, Northrhine-Westphalia (Germany), and his place of employment, an information technology company where Lousee is employed as a computer programmer. Lousee was later found in possession of a UMTS stick.
Some other circumstantial evidence also tied Lousee to the operation, such as similar login names, mentions of drugs and cryptocurrencies, and so on. (“Based on my training and experience as an investigator, I am aware that ‘420’ is a reference to marijuana,” writes the special agent who authored the complaint.)
Kalla’s VPN held strong, but the metadata betrayed him:
An IP address assigned to the home of this individual (the account for the IP address was registered in the name of the suspect’s mother) accessed VPN Provider #2 within similar rough time frames as administrator-only components of the WSM server infrastructure were accessed by VPN Provider #2.
Hardly a hole in one, but Kalla later admitted he was the user agent in question. This is a good example of how a VPN can and can’t protect you against government snooping. It may disguise your IP to certain systems, but anyone with a bird’s-eye view can see the obvious correlation between one connection and another. It won’t hold up in court on its own, but if the investigators are good it won’t have to.
Frost, the third administrator, required a more subtle approach, but ultimately it was again poor opsec, this time an unwise cross-contamination of his cryptographic and cryptocurrency accounts:
The PGP public key for [WSM administrative account] ‘TheOne’ is the same as the PGP public key for another moniker on [another hidden service] Hansa Market, ‘dudebuy.’ As described below, a financial transaction connected to a virtual currency wallet used by FROST was linked to ‘dudebuy.’
[The BKA] located the PGP public key for ‘TheOne’ in the WSM database, referred to as ‘Public Key 1’.
Public Key 1 was the PGP public key for ‘dudebuy.’ The ‘refund wallet’ for ‘dudebuy’ was Wallet 2.
Wallet 2 was a source of funds for a Bitcoin transaction… Records obtained from the Bitcoin Payment Processing Company revealed buyer information for that Bitcoin transaction as ‘Martin Frost,’ using the email address klaus-martin.frost@…
Essentially A is B, and B is C, so A is C. This little deductive trick is handy, but bitcoin wallets used by Frost were also identified through analysis by the U.S. Postal Inspection Service, which, if you didn’t know, has “a highly trained, skilled and committed cyber unit.”
The United States Postal Inspection Service learned, through its analysis of Blockchain transactions and information gleaned from the proprietary software described above, that the funds from Wallet 2 were first transferred to Wallet 1, and then “mixed” by a commercial service; mixing services is described above at paragraph 4.m. Through thorough analysis, the United States Postal Inspection Service was able to “de-mix” the flow of transactions, to eventually ascertain that the money from Wallets 1 and 2 ultimately paid FROST’s account at the Product Services Company.
Here the blockchain’s indelible record clearly worked against Frost. Wallet 1, by the way, handled thousands of bitcoins during its use in association with another darknet marketplace, German Plaza Market — which the three charged today also allegedly ran and shut down via an exit scam.
In addition to the administrators, some vendors and others associated with the site were charged. They were identified via more traditional means and their activities linked to the market in such a way that defense seems a lost cause. The record for a Brazilian man who operated as a dealer and as a sort of representative for WSM on Reddit and forums is an interesting study in the web of suggestive accounts and names that produce a damning, if circumstantial, depiction of a person’s associations and interests, from the banal to the criminal.
“The prosecution of these defendants shows that even the smallest mistake will allow us to figure out a cybercriminal’s true identity,” said U.S. Attorney McGregor W. Scott in the DOJ press release. “We are on the hunt for even the tiniest of breadcrumbs.”
Cases against the alleged criminals will be held in multiple locations and under multiple authorities — it’s safe to say this is just the beginning of a long, complicated process for everyone involved.

Source: Tech Crunch